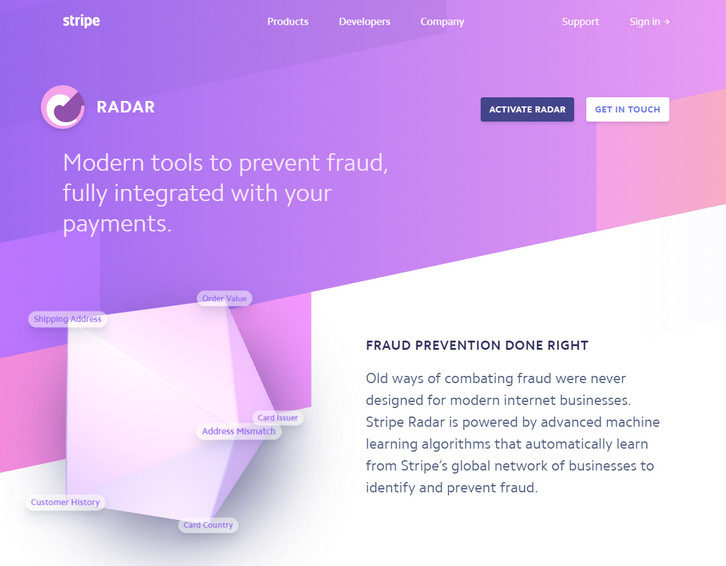
Stripe Radar is modern tools to prevent fraud, fully integrated with your payments. Old ways of combating fraud were never designed for modern internet businesses. Stripe Radar is powered by advanced machine learning algorithms that automatically learn from Stripe’s global network of businesses to identify and prevent fraud. Stripe Radar scans every transaction using the most relevant signals to detect and block fraud. And Radar’s algorithms are constantly tweaked by Stripe engineers to adapt to new fraud vectors.
They pinpoint fraud by building behavioral signals from across 100,000+ global companies. (Even if a card is new to your business, there’s an 80% chance it’s been seen before on the Stripe network.) Unlike systems that require weeks to train and only mimic human reviewers, Radar lets you instantly use rich payments data (including info from banks and card networks) to fight fraud.
Requirements: Stipe
Demo: https://stripe.com/radar
License: License Free
Skipfish is an active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes.
The resulting map is then annotated with the output from a number of active (but hopefully non-disruptive) security checks. The final report generated by the tool is meant to serve as a foundation for professional web application security assessments.

Requirements: –
Demo: https://code.google.com/p/skipfish/
License: Apache 2.0 License

jCryption is a javascript HTML-Form encryption plugin, which encrypts the POST/GET-Data that will be sent when you submit a form. It uses the Multiple-precision and Barrett modular reduction libraries for the calculations and jQuery for the rest. jCryption is completly free and dual licensed under the MIT and GPL licenses like jQuery.
Normally if you submit a form and you don’t use SSL, your data will be sent in plain text. But SSL is neither supported by every webhost nor it’s easy to install/apply sometimes. So I created this plug-in in order that you are able to encrypt your data fast and simple. jCryption uses the public-key algorithm of RSA for the encryption.
jCryption at it’s current state is no replacement for SSL, because there is no authentication, but the main goal of jCryption should be a very easy and fast to install plugin which offers a base level of security.
Requirements: jQuery Framework
Demo: http://www.jcryption.org/
License: MIT, GPL License

PHP Security Consortium (PHPSC) is an international group of PHP experts dedicated to promoting secure programming practices within the PHP community. Members of the PHPSC seek to educate PHP developers about security through a variety of resources, including documentation, tools, and standards. You can read the PHP Security Guide they have published.
In addition to their educational efforts, the PHPSC engages in exploratory and experimental research in order to develop and promote standards of best practice for PHP application development. PHP Security Consortium has developed PHPSecInfo in order to help developers and system administrators audit PHP environments.
PHPSecInfo provides an equivalent to the phpinfo() function that reports security information about the PHP environment, and offers suggestions for improvement. It is not a replacement for secure development techniques, and does not do any kind of code or app auditing, but can be a useful tool in a multilayered security approach.
Requirements: –
Demo: http://phpsec.org/projects/phpsecinfo/index.html
License: New BSD License
As security expert Bruce Schneier said recently, password masking is not a panacea. Finding a solution that provides both security and usability is the goal.
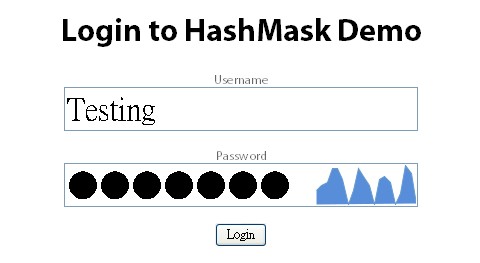
HashMask is a jQuery plugin that will produce a unique and non reversible visualization of a users password. The hope being that they would be able to confirm that they entered their password correctly, but no one else would. It also degrades gracefully so that users without javascript or a poor browser (IE6) will just see a password field.
Technically speaking, it uses a subset of the sha1 hash of the password as the seed for the sparkline’s shape and color. It should be relatively safe from reverse engineering as a result. There is the potential to estimate a possible range of characters of the first section of the hash, but overall this should be a extremely low risk.
Requirements: Javascript Enabled
Demo: http://lab.arc90.com/2009/07/hashmask.php
License: BSD License
SSL acceleration is a technique that off-loads the processor intensive public key encryption algorithms used in SSL transactions to a hardware accelerator. These solutions often involve a considerable up front investment as the specialized equipment is rather costly. o3 Magazine though looks at using off the shelf server hardware and open source software to build a cost effective SSL accelerator.
Ultimately there are two ways to do SSL Acceleration or SSL off-load. It can be done on the server side by installing an SSL Accelerator card, which has special custom processors designed to perform the public key encryption algorithms in hardware rather than software.
The other way to do SSL acceleration is to install a device in front of the web servers, this is typically an appliance or switch with comparable hardware to the SSL accelerator card. These devices often provide other features such as load balancing. They typically have higher transactions per second and thruputcapacity than a single server with an SSL accelerator card.
The Open Source SSL Accelerator requires a dedicated server running Linux. A multi-core or multi-processor system is highly recommended, with an emphasis on processing power and to a lesser degree RAM. The only software requirement is Nginx (Engine-X) which is an Open Source web server project. Nginx is designed to handle a large number of transactions per second, and has very well designed I/O subsystem code, which is what gives it a serious advantage over other options such as Lighttpd and Apache.
os Magazine has concluded that Nginx once again has shown that it is a versatile open source project. For the cost of a server and a few hours work, any system administrator can increase the capacity of their existing server farm by building an Open Source SSL Accelerator. Reducing the complexity of certificate management, reducing the number of certificates needed and reducing the overall load per request on the existing server farm, this solution offers a cost-effective way of breathing new life into an existing server farm.
Source: Open Source SSL Acceleration
Browser Security Handbook is meant to provide web application developers, browser engineers, and information security researchers with a one-stop reference to key security properties of contemporary web browsers. Insufficient understanding of these often poorly-documented characteristics is a major contributing factor to the prevalence of several classes of security vulnerabilities.
Although all browsers implement roughly the same set of baseline features, there is relatively little standardization – or conformance to standards – when it comes to many of the less apparent implementation details. Furthermore, vendors routinely introduce proprietary tweaks or improvements that may interfere with existing features in non-obvious ways, and seldom provide a detailed discussion of potential problems.
Browser Security Handbook currently covers several hundred security-relevant characteristics of Microsoft Internet Explorer (versions 6 and 7), Mozilla Firefox (versions 2 and 3), Apple Safari, Opera, Google Chrome, and Android embedded browser.
Open-source test cases provided alongside with this document permit any other browser implementations to be quickly evaluated in a similar manner.
Requirements: –
Demo: http://code.google.com/p/browsersec/
License: Apache License 2.0
Today, I have found a nice article from IBM about “Seven habits for writing secure PHP applications“. Security in a PHP application includes remote and local security concerns. Discover the habits PHP developers should get into to implement Web applications that have both characteristics.
When it comes to security, remember that in addition to actual platform and operating system security issues, you need to ensure that you write your application to be secure. When you write PHP applications, apply these seven habits to make sure your applications are as secure as possible. It includes Validate input, Guard your file system, database, session data, Guard against Cross-Site Scripting (XSS) vulnerabilities, Verify form posts and Protect against Cross-Site Request Forgeries (CSRF).
Source: Seven habits for writing secure PHP applications

Suhosin is an advanced protection system for PHP installations. It was designed to protect servers and users from known and unknown flaws in PHP applications and the PHP core. Suhosin comes in two independent parts, that can be used separately or in combination. The first part is a small patch against the PHP core, that implements a few low-level protections against bufferoverflows or format string vulnerabilities and the second part is a powerful PHP extension that implements all the other protections.
If you are using PHP only for your own server and only for your own scripts and applications, then you can judge for yourself, if you trust your code enough. In that case you most probably don’t need the Suhosin extension. Because most of it’s features are meant to protect servers against vulnerable programming techniques. However PHP is a very complex programming language with a lot of pitfalls that are often overseen during the development of applications. Even PHP core programmers are writing insecure code from time to time, because they did not know about a PHP pitfall. Therefore it is always a good idea to have Suhosin as your safety net.
P.S. Suhosin (ìˆ˜í˜¸ì‹ ) is a south-korean word that means something very similiar to the english guardian-angel.
Requirements: –
Demo: http://www.hardened-php.net/suhosin/
License: PHP License 3.01
Just a quick reminder that tomorrow is the last day for you to submit your work for Web Design Contest with $1,000 Cash Prize. Good Luck~
Ratproxy is a semi-automated, largely passive web application security audit tool. It is meant to complement active crawlers and manual proxies more commonly used for this task, and is optimized specifically for an accurate and sensitive detection, and automatic annotation, of potential problems and security-relevant design patterns based on the observation of existing, user-initiated traffic in complex web 2.0 environments. The approach taken with ratproxy offers several important advantages over more traditional methods:
- No risk of disruptions. In the default operating mode, tool does not generate a high volume of attack-simulating traffic, and as such may be safely employed against production systems at will, for all types of ad hoc, post-release audits. Active scanners may trigger DoS conditions or persistent XSSes, and hence are poorly suited for live platforms.
- Low effort, high yield. Compared to active scanners or fully manual proxy-based testing, ratproxy assessments take very little time or bandwidth to run, and proceed in an intuitive, distraction-free manner – yet provide a good insight into the inner workings of a product, and the potential security vulnerabilities therein. They also afford a consistent and predictable coverage of user-accessible features.
- Preserved control flow of human interaction. By silently following the browser, the coverage in locations protected by nonces, during other operations valid only under certain circumstances, or during dynamic events such as cross-domain Referer data disclosure, is greatly enhanced. Brute-force crawlers and fuzzers usually have no way to explore these areas in a reliable manner.
- WYSIWYG data on script behavior. Javascript interfaces and event handlers are explored precisely to a degree they are used in the browser, with no need for complex guesswork or simulations. Active scanners often have a significant difficulty exploring JSON responses, XMLHttpRequest() behavior, UI-triggered event data flow, and the like.
- Easy process integration. The proxy can be transparently integrated into an existing manual security testing or interface QA processes without introducing a significant setup or operator training overhead.

Requirements: –
Demo: http://code.google.com/p/ratproxy/
License: Apache License 2.0